Configuring Passwordless Authentication
- Login to the instasafe console as an admin
- Click on AUTHENTICATION PROFILE >> Passwordless
- Click on Add Button

-
Enter a Profile name and Select primary Auth as Hardware key and Fallback Passwordles Auth option as password.
-
Click on the Save and Add New button

- Now the profile will list over the passwordless page
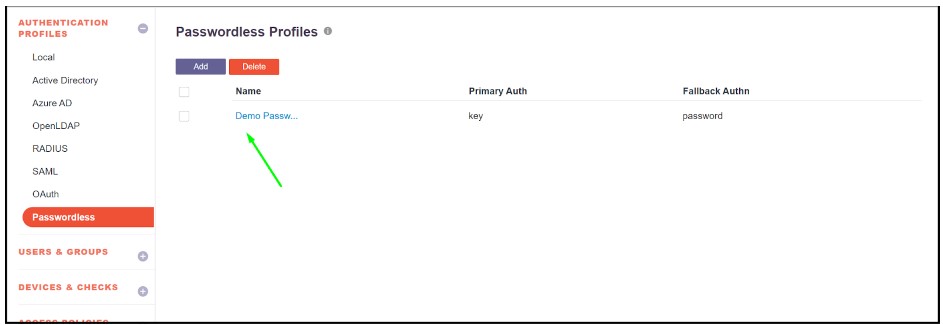
- After the successful creation of a passwordless Profile that can be used for a single user or a User Group.
- To assign that passwordless in the user profile click on USERS & GROUPS >> Users
- Search for the user and select the user which will be assigned to a passwordless profile
- Click on the Edit button

- Click on the Authentication Profile and select the passwordless profile which was created earlier.
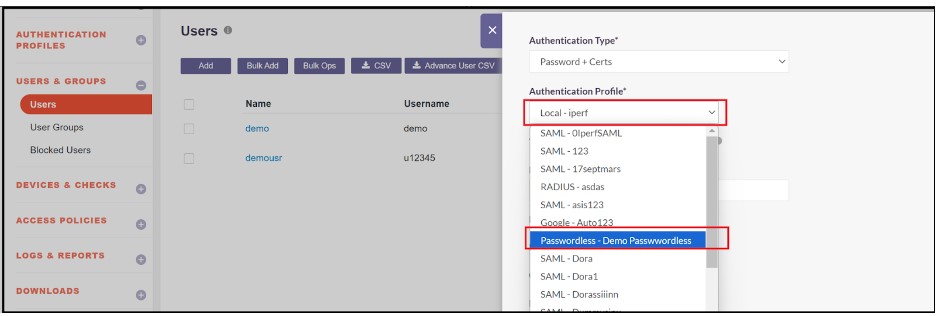
- Click on the Update button to save the Authentication profile of the User as passwordless.

- To assign that passwordless in the UserGroup profile click on USERS & GROUPS >> Users
- Search for UserGroup and select the UserGroup which will assign to a passwordless profile.
- Click on the Edit button

- Click on the Authentication Profile and select the passwordless profile which was created earlier.
- Click on the Update button to save the Authentication profile of UserGroup as passwordless which will apply to all the members of the group as passwordless authentication

- Login to the instance console with the user which enabled passwordless Authentication
- Click on the profile icon. Then click on the MFA option

- Now click on the Resister key under FIDO Keys
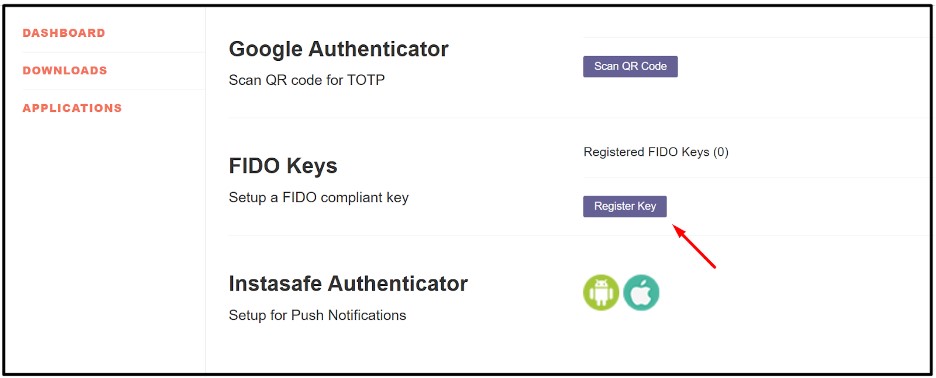
- For Windows hello option will display user can choose either the hello option or the Hardware key by clicking on the use another device option
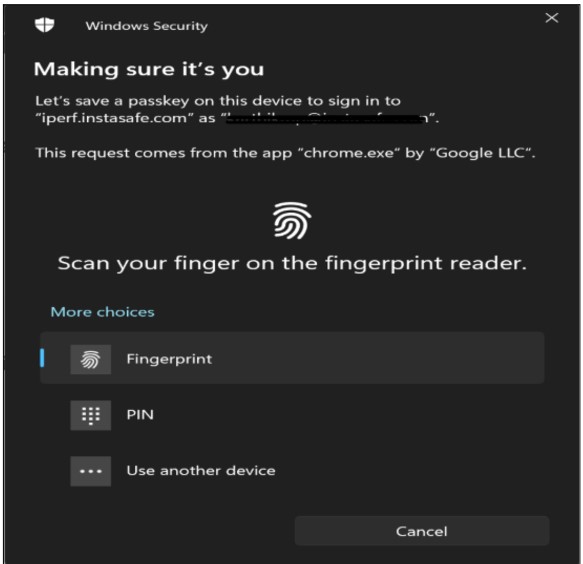
After verifying/adding the hello it will save and allow the user to login via passwordless
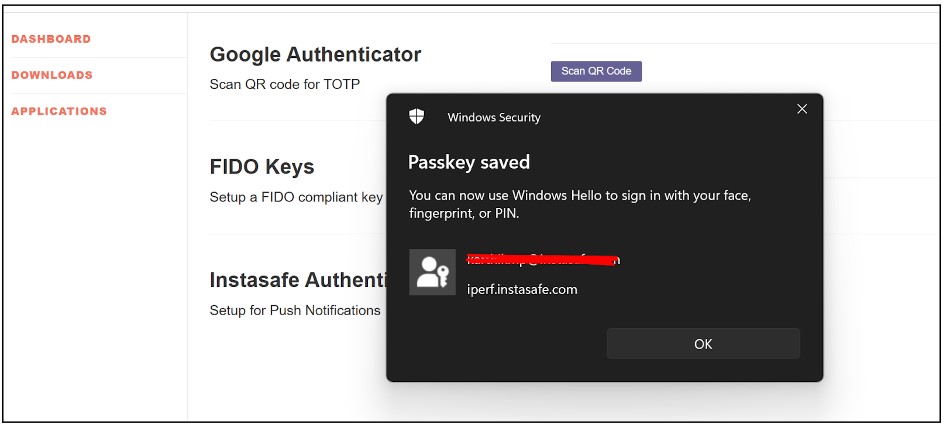
- After the successful registration of the hardware key, Hardware key registered successfully message will display

Console Login Through The Passwordless Hardware Key
- After successfully registering the hardware key, when the User logs in Next time, it will directly ask for the Hardware key instead of the password
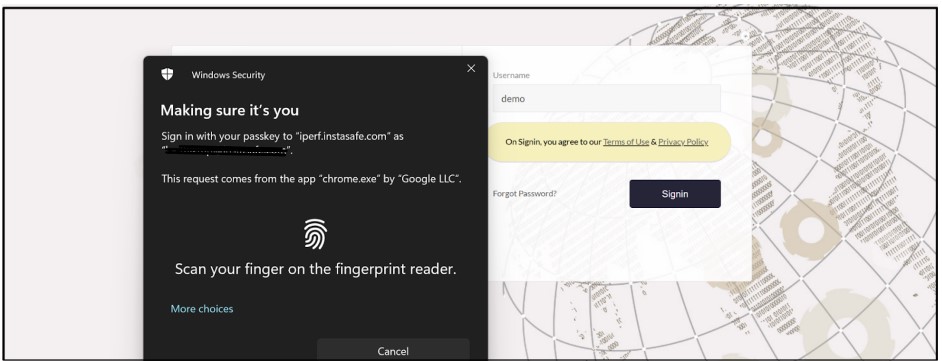
- The user will log in to instasafe after verification of the Hardware Key

Configuring Passwordless Authentication with Digital Certificate
- Login to the instasafe console as an admin credential
- Click on AUTHENTICATION PROFILE >> Passwordless
- Now click on Add Button

- Enter a Profile name and Select primary Auth as Digital Certificate and Fallback Auth option as password
- Now click on the Save and AddNew button
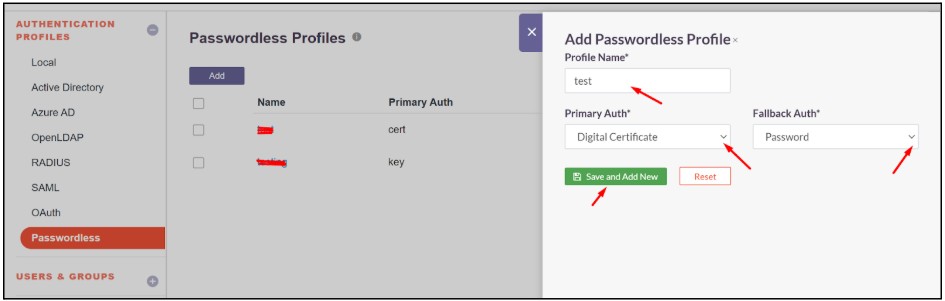
- Now the profile will list over the Passwordless page
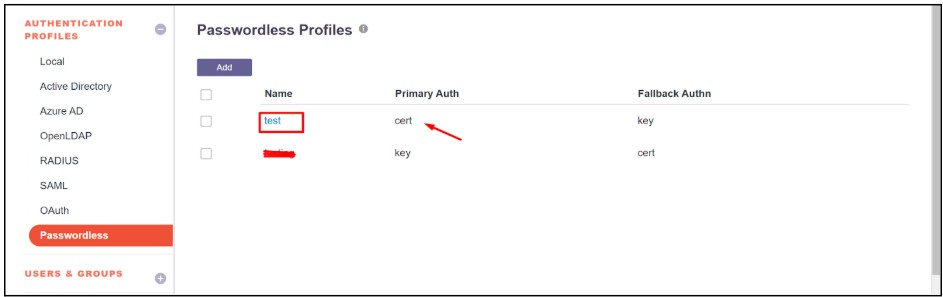
- After the successful creation of a passwordless profile, it can be used for a single user or a User Group.
- To assign that passwordless in the user profile, click on USERS & GROUPS >> Users
- Search for the user and select the user which will be assigned to a passwordless profile
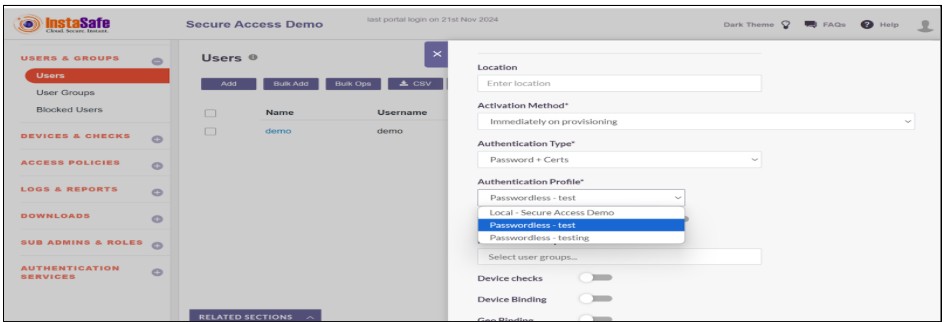
- Now click on the Edit button
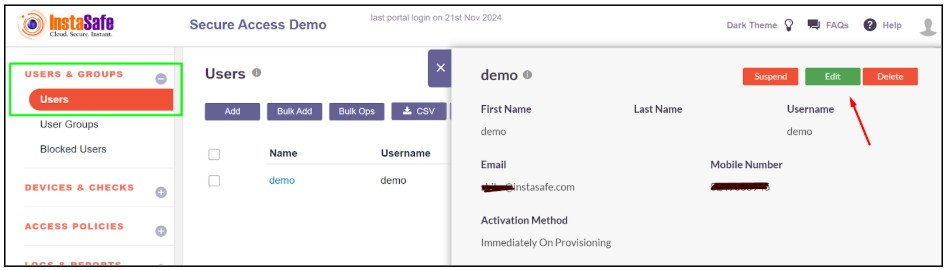
- Now choose the passwordless profile with a digital certificate.
Installation Process of Digital Certificate
- Login to the instasafe console with the user for which the passwordless digital certificate authentication is configured.
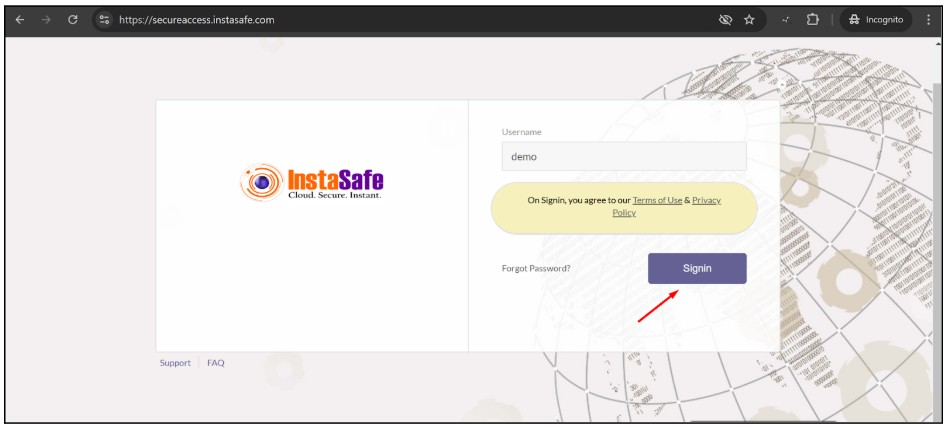
- Enter the password and click on sign in
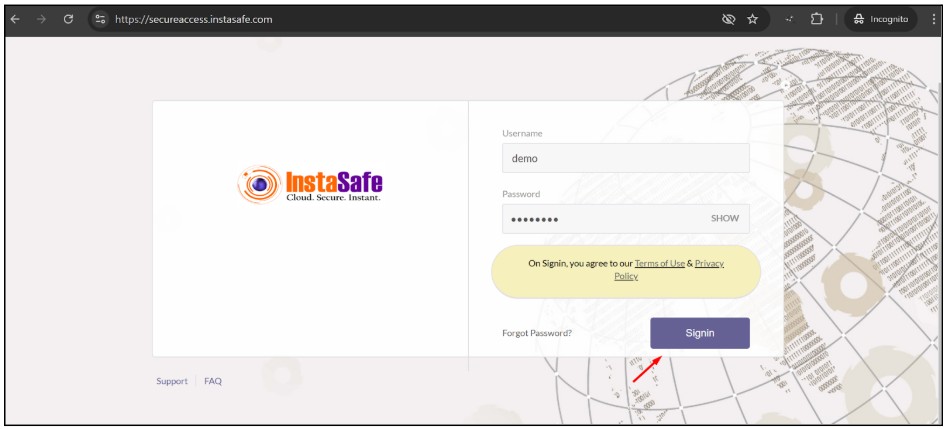
- After Successful login Navigate to the Download section in the Dashboard Menu
- Download the instasafe web agent
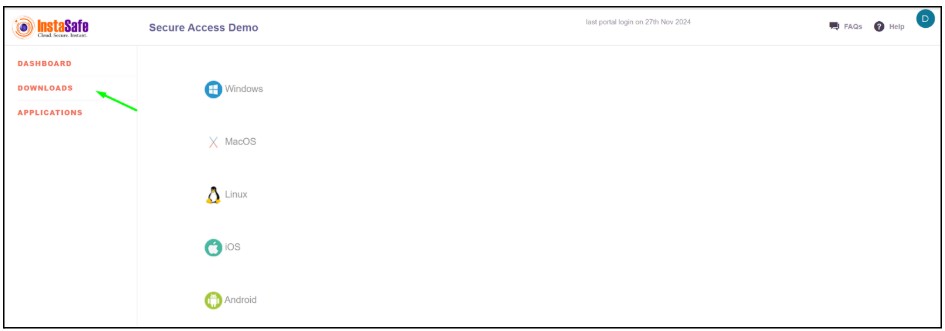
- Install the web agent to set up the digital certificate
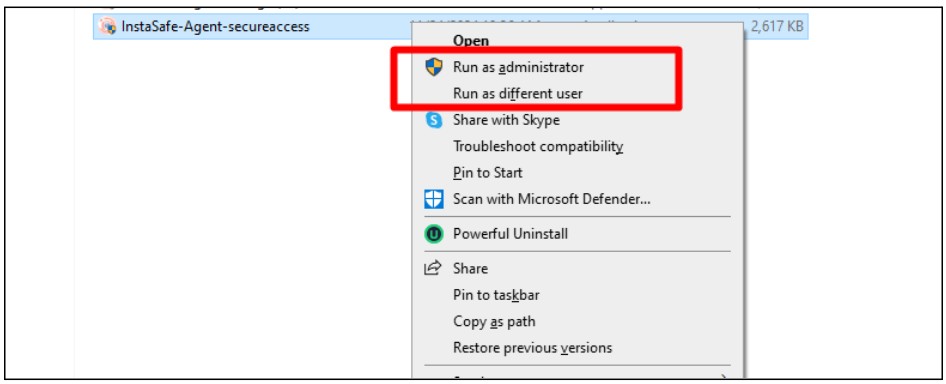
- Enter the credential of a user for which the digital certificate is configured and click on login
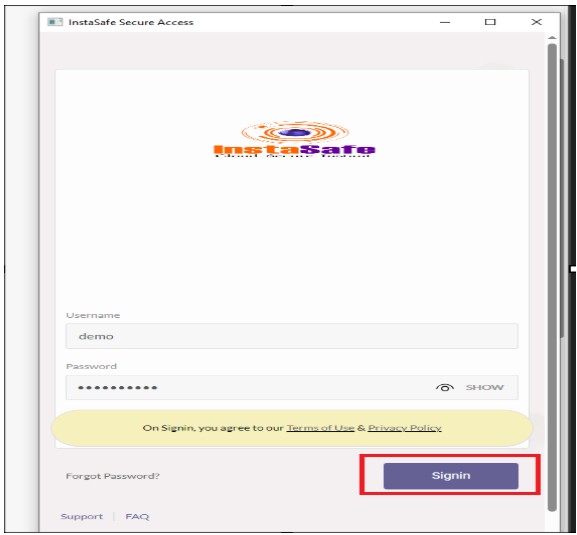
- After the Successful installation of the agent installation, a success message will appear
- Then click on the ok button of the pop-up message
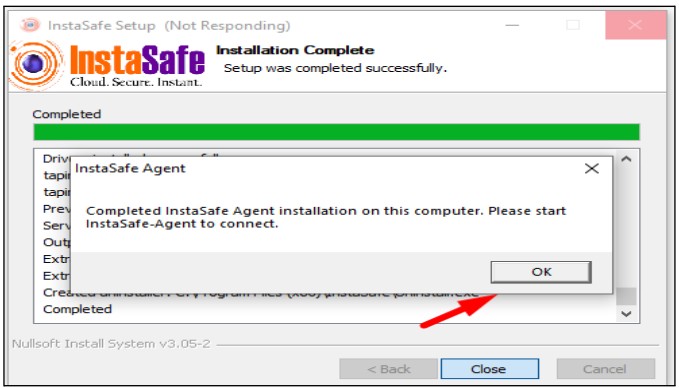
Instasafe Agent access with Digital certificate
- After the agent is installed, the digital certificate will be installed on the computer.
- Enter the URL in the browser
- A certificate prompt will open for Digital certificate passwordless authentication click on ok
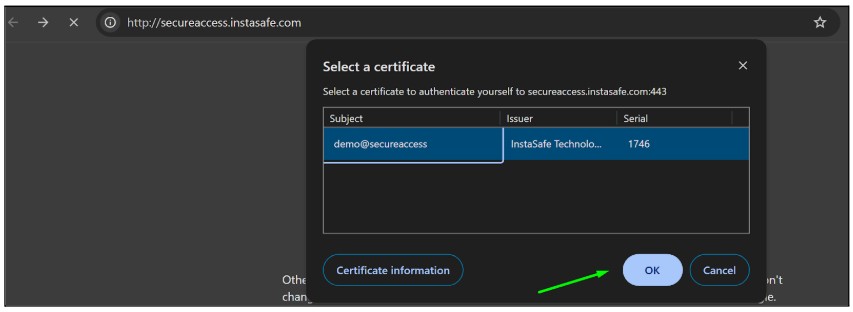
- After clicking on the ok, the login page will appear.
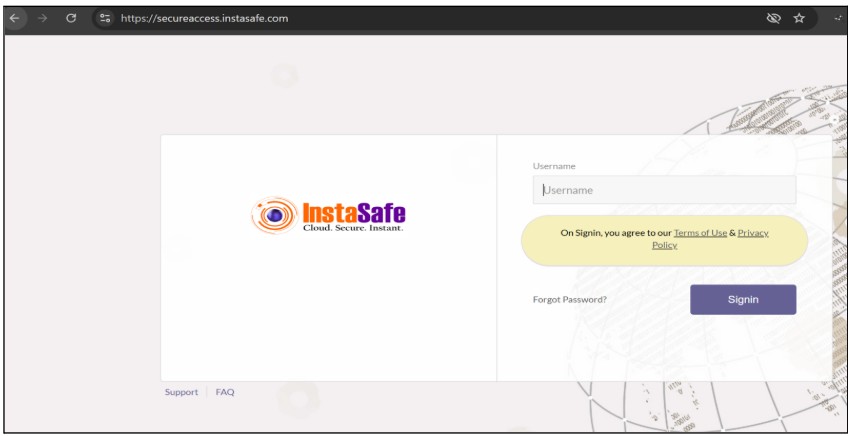
- Now enter your username and click on sign in.
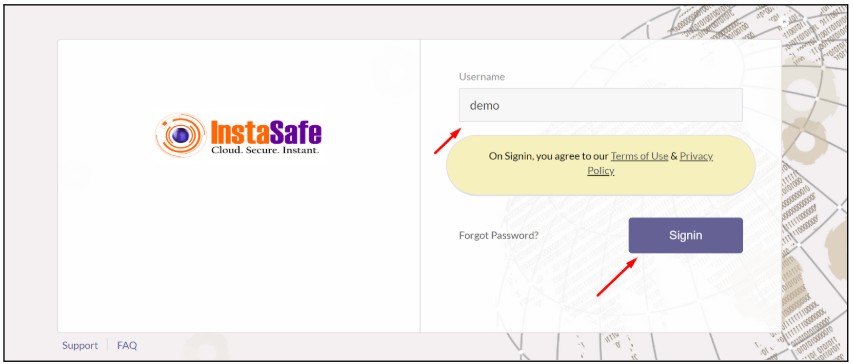
- The user will be directly redirected to the dashboard page without asking for any password
Instasafe Agent access with Digital certificate
- After the installation of the agent when the user tries to log in next time Then the certificate will appear
- Select the certificate and click on ok for passwordless digital certificate-based login

- Now enter the username which is configured for passwordless and click on sign in
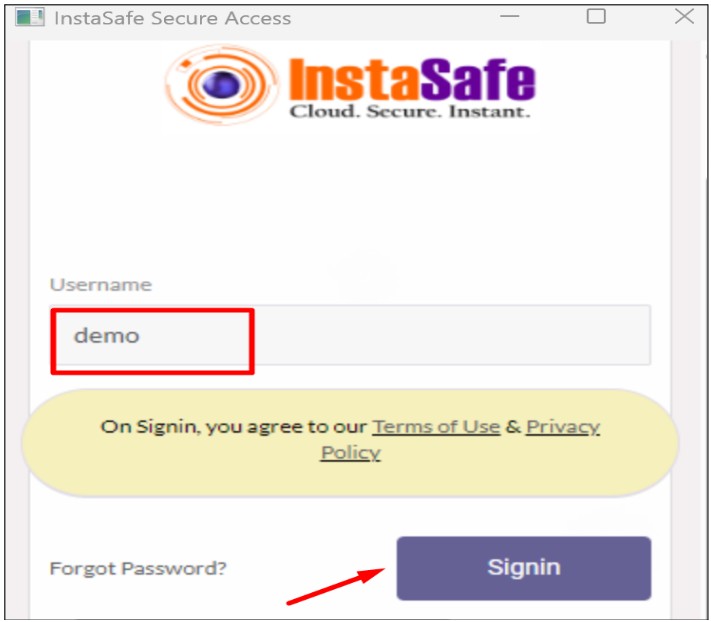
- After sign-in, the user will connect to the agent successfully without asking for the Password