Domain Joining
DOMAIN JOINING
Workforce today, is becoming increasingly mobile and dynamic. They expect that the individuals should not be confined to an office and should have the freedom and ability to work remotely.Over the years, IT Admins have relied on directory services like AD (Active Directory) to make the workforce compliant to the company policies. However, in today’s scenario, it becomes very difficult to make the remote workers comply with the policy, as the directory services can only be implemented on On-Premise users. InstaSafe ZTAA empowers the IT teams to make the remote devices join the corporate domain, so they can then easily push policies using AD(Active Directory).
Prerequisites-
-
TCP Gateway should be added and Directory Sync Profile should be added and then synced.
-
Network Gateway (Version 3.6.2+ ) should be added in console.
-
Domain joining is not available for devices with Windows HOME Edition installed.
Steps to Configure
-
Login to ZTAA console as an admin
-
Create a Network application with the domain of AD-Server(eg. instalocal.local).
-
Select protocol as ALL.Give IP adress field as AD-Server Private IP .Allow Port over which you want the connection to be establised. If unsure you can choose to allow all ports (1-65535 as open.)
-
After creation of the application Add it into the network gateway and change the DNS server value of gateway to ADServer private IP.If the DNS server value is not set as that of the AD server IP then after the VPN tunnel is established, the DNS resolution would be incorrect.
-
Add the Network application into an ACL which is associated with your user.
Connect User to Domain
-
Go to control panel >> system security >> system
-
Click on Advance Setting >> click computer name
-
Click on change button of rename computer
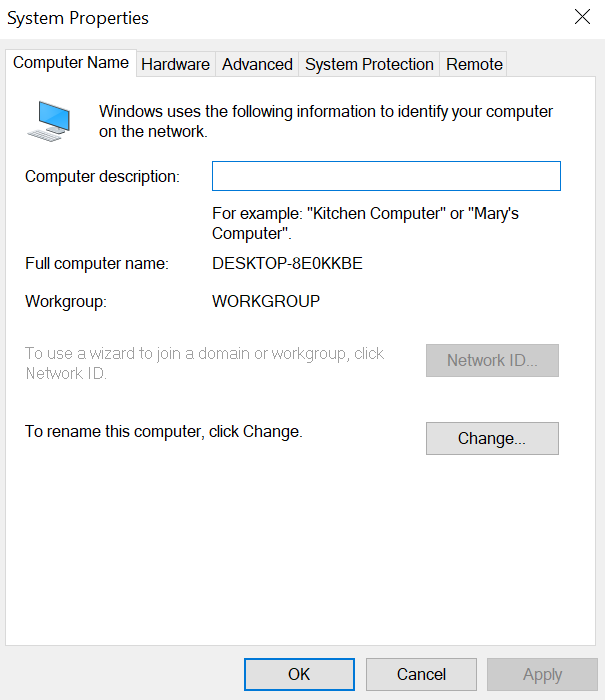
- Click on the member of select domain instead of the workgroup and give domain name as Your ADServer domain name(instalocal.local) >> click on ok
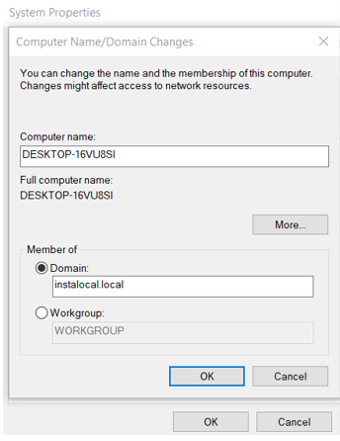
- Provide the domain administrator credentials in the following format: domain\ad_username ( instalocal\administrator) and password.
On Successful Configuration a Welcome Popup message will be displayed.
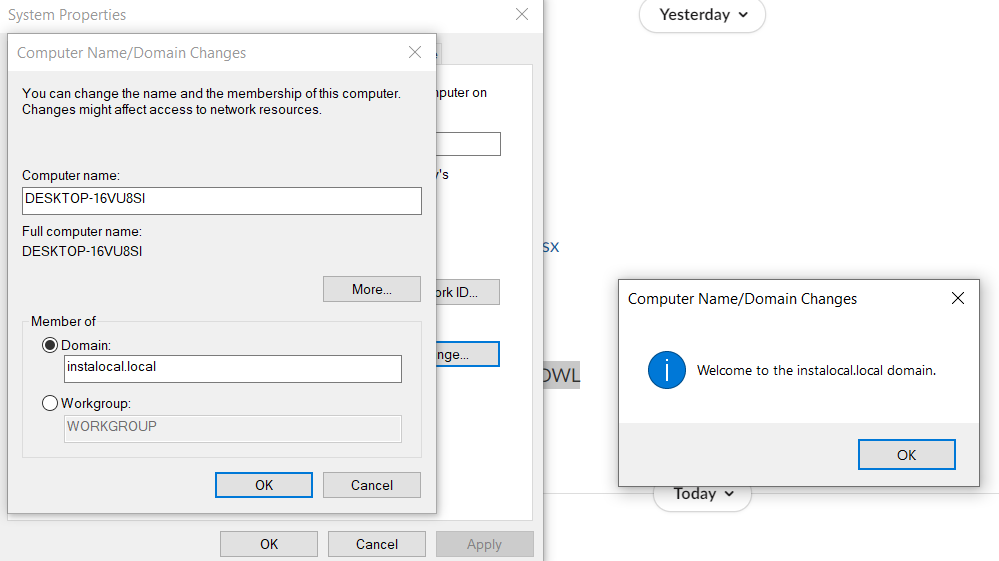
Verify Successful Connection
- Login into the AD Server.
- In case of successful domain joining the user device will be visible in the ADServer.
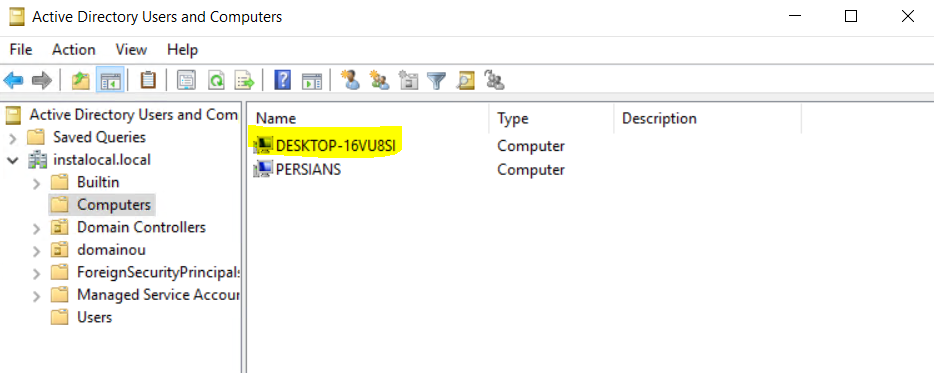
Creating ACL rules based on system Domain
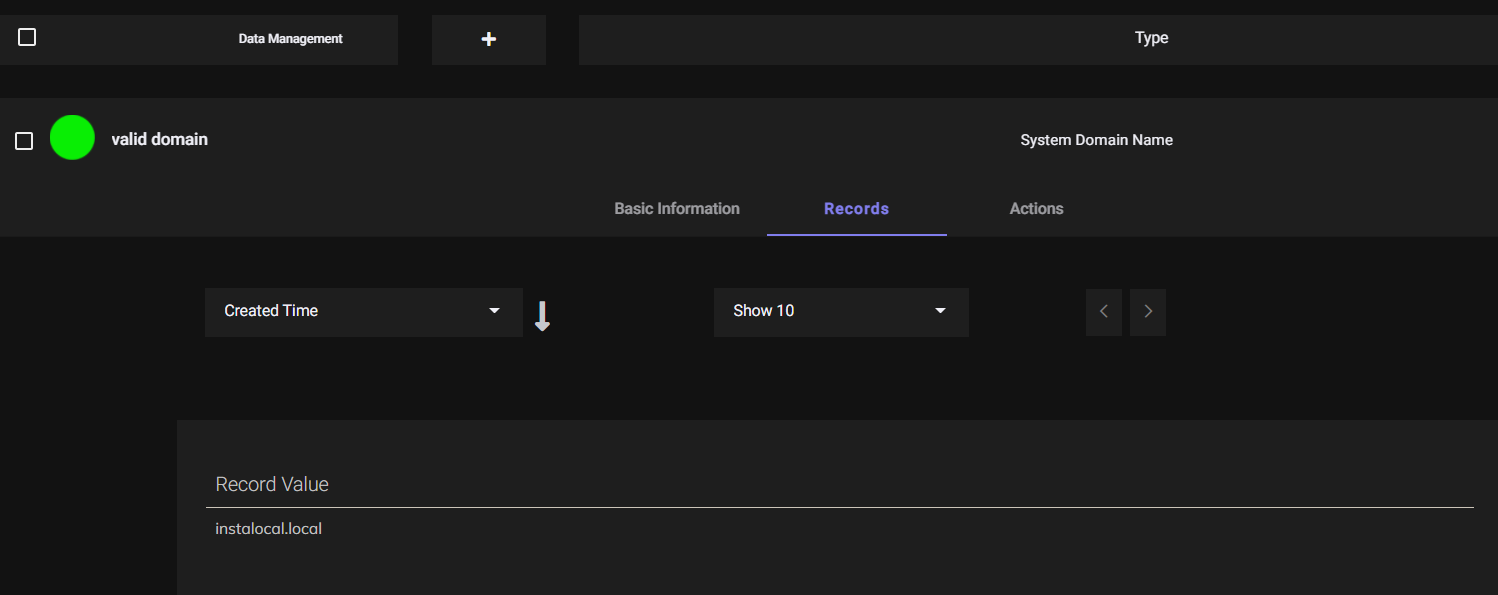
- Create a Dataset with System Domain Name as Datatype and value as domain name to which the system is to be joined.
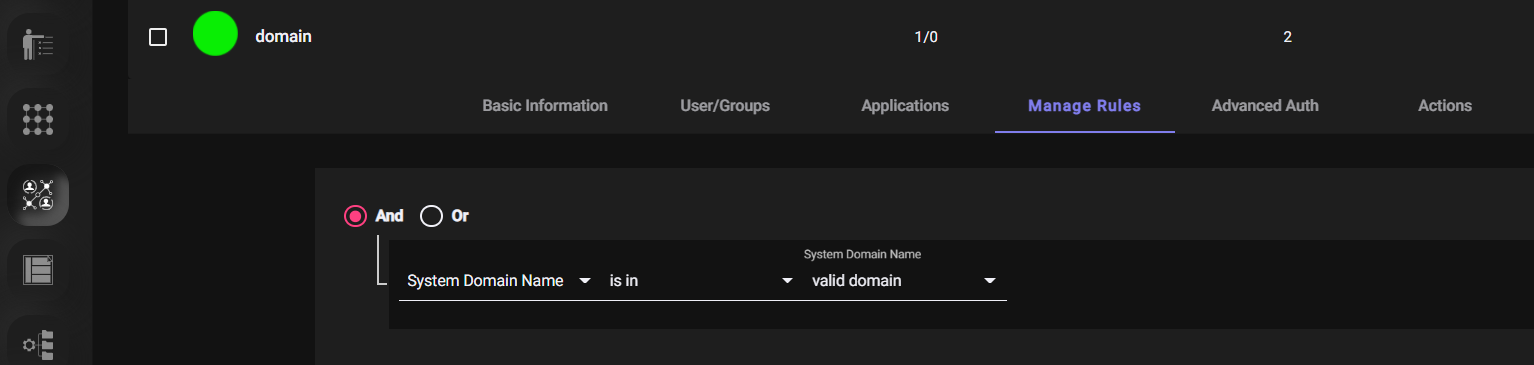
- Create an ACL with rule System Domain Name isin valid domain.
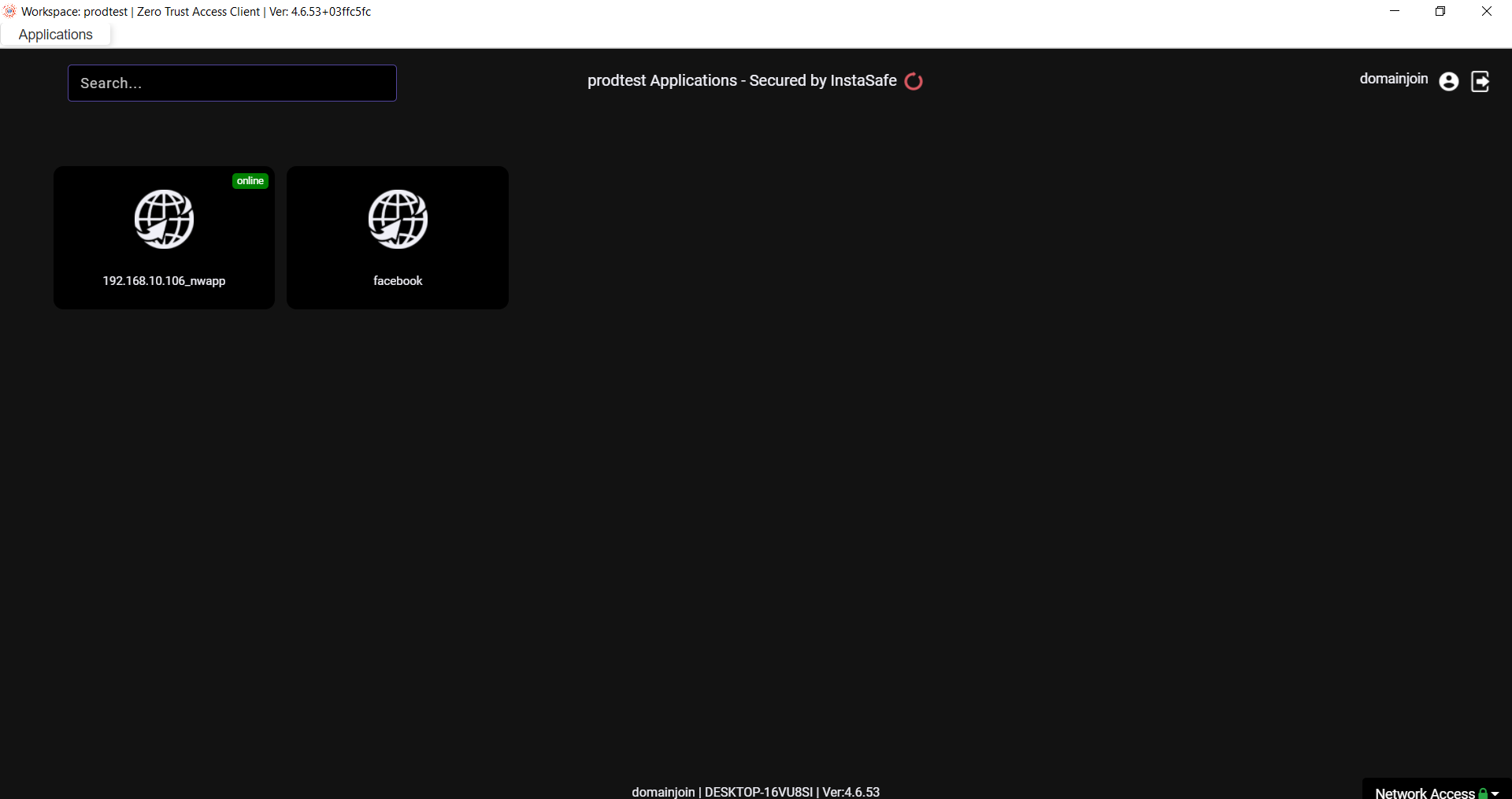
- Now only the configured application will be visible to the user if his/her system is joined to the required domain.
DOMAIN JOINED SYSTEM
SYSTEM WHICH ARE NOT JOINED WITH DOMAIN